Browsing Category
Threats
11 posts
Auto Added by WPeMatico
Pegasus Spyware Used Widely to Target Individuals in Private Industry & Finance Sectors
Pegasus spyware, once considered a tool for targeting journalists and activists—is now being deployed against executives in the…
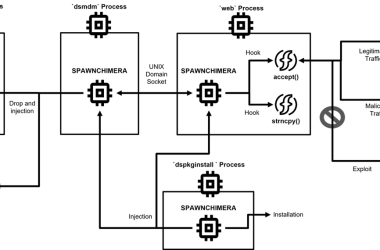
SPAWNCHIMERA Malware Exploiting Ivanti Buffer Overflow Vulnerability By Applying A Fix
Ivanti disclosed a critical buffer overflow vulnerability (CVE-2025-0282) affecting its Connect Secure VPN appliances. This vulnerability, caused by…
Chinese Hackers Using New Bookworm Malware In Attacks Targeting Southeast Asia
Security researchers at Palo Alto Networks’ Unit 42 have uncovered a resurgence of the modular Bookworm malware in…
New NailaoLocker Ransomware Attacking European Healthcare
European healthcare organizations are facing a sophisticated cyber threat from a newly identified ransomware strain called NailaoLocker, deployed…
New Wave of ‘Scam-Yourself’ Attacks Utilizing AI-Generated Videos With DeepFake
A new wave of “Scam-Yourself” attacks leveraging AI-generated deepfake videos and malicious scripts is targeting cryptocurrency enthusiasts and…
Weaponized Signal, Line, and Gmail Apps Delivers Malware That Changes System Defenses
A sophisticated cyberattack campaign targeting Chinese-speaking users, malicious actors have weaponized fake versions of popular applications such as…
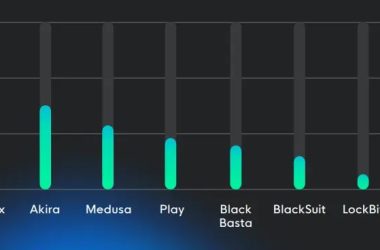
Ransomware Gangs Encrypt Systems After 17hrs From Initial Infection
New research reveals ransomware gangs are accelerating encryption timelines while adopting advanced evasion techniques and data extortion strategies.…
Hidden Malware in WordPress Websites Allows Attackers to Execute Malicious Code Remotely
A sophisticated malware campaign has recently been uncovered by security researchers at Sucuri, targeting WordPress websites through hidden…
Beware of Fake Outlook Troubleshooting Calls that Ends Up In Ransomware Deployment
A sophisticated cyber threat has emerged in recent weeks, targeting unsuspecting users with fake Outlook troubleshooting calls. These…
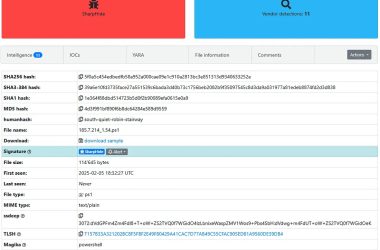
Threat Actors Leveraging Modified Version of SharpHide Tool To Create Hidden Registry
Threat actors have been utilizing a modified version of the SharpHide tool to create hidden registry values, significantly…